Write-up for Bandit
Level 0
The goal of this level is for you to log into the game using SSH. The host to which you need to connect is bandit.labs.overthewire.org, on port 2220. The username is bandit0 and the password is bandit0. Once logged in, go to the Level 1 page to find out how to beat Level 1.
$ ssh bandit0@bandit.labs.overthewire.org -p 2220
This is a OverTheWire game server. More information on http://www.overthewire.org/wargames
bandit0@bandit.labs.overthewire.org password: bandit0
Linux bandit.otw.local 5.4.8 x86_64 GNU/Linux
Welcome to OverTheWire!
Enjoy your stay!
bandit0@bandit:~$ whoami
bandit0Level 0 to 1
The password for the next level is stored in a file called readme located in the home directory. Use this password to log into bandit1 using SSH. Whenever you find a password for a level, use SSH (on port 2220) to log into that level and continue the game.
bandit0@bandit:~$ ls -la
total 24
drwxr-xr-x 2 root root 4096 May 7 2020 .
drwxr-xr-x 41 root root 4096 May 7 2020 ..
-rw-r--r-- 1 root root 220 May 15 2017 .bash_logout
-rw-r--r-- 1 root root 3526 May 15 2017 .bashrc
-rw-r--r-- 1 root root 675 May 15 2017 .profile
-rw-r----- 1 bandit1 bandit0 33 May 7 2020 readme
bandit0@bandit:~$ cat readme
boJ9jbbUNNfktd78OOpsqOltutMc3MY1Level 1 to 2
The password for the next level is stored in a file called - located in the home directory.
bandit1@bandit:~$ ls
-
bandit1@bandit:~$ cat ./-
CV1DtqXWVFXTvM2F0k09SHz0YwRINYA9Level 2 to 3
The password for the next level is stored in a file called spaces in this filename located in the home directory.
bandit2@bandit:~$ ls
spaces in this filename
bandit2@bandit:~$ cat "spaces in this filename"
UmHadQclWmgdLOKQ3YNgjWxGoRMb5luK
bandit2@bandit:~$ cat spaces\ in\ this\ filename
UmHadQclWmgdLOKQ3YNgjWxGoRMb5luKLevel 3 to 4
The password for the next level is stored in a hidden file in the inhere directory.
bandit3@bandit:~$ ls
inhere
bandit3@bandit:~$ cd inhere
bandit3@bandit:~/inhere$ ls
bandit3@bandit:~/inhere$ ls -la
total 12
drwxr-xr-x 2 root root 4096 May 7 2020 .
drwxr-xr-x 3 root root 4096 May 7 2020 ..
-rw-r----- 1 bandit4 bandit3 33 May 7 2020 .hidden
bandit3@bandit:~/inhere$ cat .hidden
pIwrPrtPN36QITSp3EQaw936yaFoFgABLevel 4 to 5
The password for the next level is stored in the only human-readable file in the inhere directory.
bandit4@bandit:~/inhere$ cd ..
bandit4@bandit:~$ clear
bandit4@bandit:~$ ls
inhere
bandit4@bandit:~$ cd inhere
bandit4@bandit:~/inhere$ ls -la
total 48
drwxr-xr-x 2 root root 4096 May 7 2020 .
drwxr-xr-x 3 root root 4096 May 7 2020 ..
-rw-r----- 1 bandit5 bandit4 33 May 7 2020 -file00
-rw-r----- 1 bandit5 bandit4 33 May 7 2020 -file01
-rw-r----- 1 bandit5 bandit4 33 May 7 2020 -file02
-rw-r----- 1 bandit5 bandit4 33 May 7 2020 -file03
-rw-r----- 1 bandit5 bandit4 33 May 7 2020 -file04
-rw-r----- 1 bandit5 bandit4 33 May 7 2020 -file05
-rw-r----- 1 bandit5 bandit4 33 May 7 2020 -file06
-rw-r----- 1 bandit5 bandit4 33 May 7 2020 -file07
-rw-r----- 1 bandit5 bandit4 33 May 7 2020 -file08
-rw-r----- 1 bandit5 bandit4 33 May 7 2020 -file09
bandit4@bandit:~/inhere$ file ./-file*
./-file00: data
./-file01: data
./-file02: data
./-file03: data
./-file04: data
./-file05: data
./-file06: data
./-file07: ASCII text
./-file08: data
./-file09: data
bandit4@bandit:~/inhere$ cat ./-file07
koReBOKuIDDepwhWk7jZC0RTdopnAYKhLevel 5 to 6
The password for the next level is stored in a file somewhere under the inhere directory and has all of the following properties:
- human-readable
- 1033 bytes in size
- not executable
bandit5@bandit:~$ ls
inhere
bandit5@bandit:~$ cd inhere
bandit5@bandit:~/inhere$ ls
maybehere00 maybehere03 maybehere06 maybehere09 maybehere12 maybehere15 maybehere18
maybehere01 maybehere04 maybehere07 maybehere10 maybehere13 maybehere16 maybehere19
maybehere02 maybehere05 maybehere08 maybehere11 maybehere14 maybehere17
bandit5@bandit:~/inhere$ find . -type f -readable -size 1033c ! -executable
./maybehere07/.file2
bandit5@bandit:~/inhere$ cat ./maybehere07/.file2
DXjZPULLxYr17uwoI01bNLQbtFemEgo7Level 6 to 7
The password for the next level is stored somewhere on the server and has all of the following properties:
- owned by user bandit7
- owned by group bandit6
- 33 bytes in size
bandit6@bandit:~$ cd /
bandit6@bandit:/$ find . -user bandit7 -group bandit6 -size 33c
find: ‘./root’: Permission denied
find: ‘./home/bandit28-git’: Permission denied
find: ‘./home/bandit30-git’: Permission denied
find: ‘./home/bandit5/inhere’: Permission denied
find: ‘./home/bandit27-git’: Permission denied
find: ‘./home/bandit29-git’: Permission denied
find: ‘./home/bandit31-git’: Permission denied
find: ‘./lost+found’: Permission denied
find: ‘./etc/ssl/private’: Permission denied
find: ‘./etc/polkit-1/localauthority’: Permission denied
find: ‘./etc/lvm/archive’: Permission denied
find: ‘./etc/lvm/backup’: Permission denied
find: ‘./sys/fs/pstore’: Permission denied
find: ‘./proc/tty/driver’: Permission denied
find: ‘./proc/5355/task/5355/fd/6’: No such file or directory
find: ‘./proc/5355/task/5355/fdinfo/6’: No such file or directory
find: ‘./proc/5355/fd/5’: No such file or directory
find: ‘./proc/5355/fdinfo/5’: No such file or directory
find: ‘./cgroup2/csessions’: Permission denied
find: ‘./boot/lost+found’: Permission denied
find: ‘./tmp’: Permission denied
find: ‘./run/lvm’: Permission denied
find: ‘./run/screen/S-bandit0’: Permission denied
find: ‘./run/screen/S-bandit16’: Permission denied
find: ‘./run/screen/S-bandit33’: Permission denied
find: ‘./run/screen/S-bandit5’: Permission denied
find: ‘./run/screen/S-bandit11’: Permission denied
find: ‘./run/screen/S-bandit20’: Permission denied
find: ‘./run/screen/S-bandit13’: Permission denied
find: ‘./run/screen/S-bandit29’: Permission denied
find: ‘./run/screen/S-bandit25’: Permission denied
find: ‘./run/screen/S-bandit30’: Permission denied
find: ‘./run/screen/S-bandit9’: Permission denied
find: ‘./run/screen/S-bandit28’: Permission denied
find: ‘./run/screen/S-bandit18’: Permission denied
find: ‘./run/screen/S-bandit7’: Permission denied
find: ‘./run/screen/S-bandit26’: Permission denied
find: ‘./run/screen/S-bandit15’: Permission denied
find: ‘./run/screen/S-bandit4’: Permission denied
find: ‘./run/screen/S-bandit19’: Permission denied
find: ‘./run/screen/S-bandit31’: Permission denied
find: ‘./run/screen/S-bandit17’: Permission denied
find: ‘./run/screen/S-bandit22’: Permission denied
find: ‘./run/screen/S-bandit21’: Permission denied
find: ‘./run/screen/S-bandit14’: Permission denied
find: ‘./run/screen/S-bandit24’: Permission denied
find: ‘./run/screen/S-bandit23’: Permission denied
find: ‘./run/shm’: Permission denied
find: ‘./run/lock/lvm’: Permission denied
find: ‘./var/spool/bandit24’: Permission denied
find: ‘./var/spool/cron/crontabs’: Permission denied
find: ‘./var/spool/rsyslog’: Permission denied
find: ‘./var/tmp’: Permission denied
find: ‘./var/lib/apt/lists/partial’: Permission denied
find: ‘./var/lib/polkit-1’: Permission denied
./var/lib/dpkg/info/bandit7.password
find: ‘./var/log’: Permission denied
find: ‘./var/cache/apt/archives/partial’: Permission denied
find: ‘./var/cache/ldconfig’: Permission denied
bandit6@bandit:/$ cat ./var/lib/dpkg/info/bandit7.password
HKBPTKQnIay4Fw76bEy8PVxKEDQRKTzsLevel 7 to 8
The password for the next level is stored in the file data.txt next to the word millionth.
bandit7@bandit:~$ ls
data.txt
bandit7@bandit:~$ grep millionth data.txt
millionth cvX2JJa4CFALtqS87jk27qwqGhBM9plVLevel 8 to 9
The password for the next level is stored in the file data.txt and is the only line of text that occurs only once.
bandit8@bandit:~$ ls
data.txt
bandit8@bandit:~$ sort data.txt | uniq -cu
1 UsvVyFSfZZWbi6wgC7dAFyFuR6jQQUhRLevel 9 to 10
The password for the next level is stored in the file data.txt in one of the few human-readable strings, preceded by several ‘=’ characters.
bandit9@bandit:~$ ls
data.txt
bandit9@bandit:~$ strings data.txt | grep "=="
========== the*2i 4
========== password
Z)========== is
&========== truKLdjsbJ5g7yyJ2X2R0o3a5HQJFuLkLevel 10 to 11
The password for the next level is stored in the file data.txt, which contains base64 encoded data.
bandit10@bandit:~$ ls
data.txt
bandit10@bandit:~$ cat data.txt
VGhlIHBhc3N3b3JkIGlzIElGdWt3S0dzRlc4TU9xM0lSRnFyeEUxaHhUTkViVVBSCg==
bandit10@bandit:~$ base64 -d data.txt
The password is IFukwKGsFW8MOq3IRFqrxE1hxTNEbUPRLevel 11 to 12
The password for the next level is stored in the file data.txt, where all lowercase (a-z) and uppercase (A-Z) letters have been rotated by 13 positions.
bandit11@bandit:~$ ls
data.txt
bandit11@bandit:~$ cat data.txt | tr 'A-M N-Z a-m n-z' 'N-Z A-M n-z a-m'
The password is 5Te8Y4drgCRfCx8ugdwuEX8KFC6k2EUuLevel 12 to 13
The password for the next level is stored in the file data.txt, which is a hexdump of a file that has been repeatedly compressed.
bandit12@bandit:~$ ls
data.txt
bandit12@bandit:~$ mkdir /tmp/level12/
mkdir: cannot create directory ‘/tmp/level12/’: File exists
bandit12@bandit:~$ cp data.txt /tmp/level12/
bandit12@bandit:~$ cd /tmp/level12/
bandit12@bandit:/tmp/level12$ ls
data.txt
bandit12@bandit:~$ file data.txt
data.txt: ASCII text
bandit12@bandit:~$ mkdir /tmp/level12/
bandit12@bandit:~$ cp data.txt /tmp/level12/
bandit12@bandit:~$ cd /tmp/level12/
bandit12@bandit:/tmp/level12$ ls
data.txt
bandit12@bandit:/tmp/level12$ xxd -r data.txt data
bandit12@bandit:/tmp/level12$ ls
data data.txt
bandit12@bandit:/tmp/level12$ file data
data: gzip compressed data, was "data2.bin", last modified: Thu May 7 18:14:30 2020, max compression, from Unix
bandit12@bandit:/tmp/level12$ mv data data.gz
bandit12@bandit:/tmp/level12$ gzip -d data.gz
bandit12@bandit:/tmp/level12$ ls
data data.txt
bandit12@bandit:/tmp/level12$ file data
data: bzip2 compressed data, block size = 900k
bandit12@bandit:/tmp/level12$ mv data data.bz2
bandit12@bandit:/tmp/level12$ bzip2 -d data.bz2
bandit12@bandit:/tmp/level12$ file data
data: gzip compressed data, was "data4.bin", last modified: Thu May 7 18:14:30 2020, max compression, from Unix
bandit12@bandit:/tmp/level12$ mv data data.gz
bandit12@bandit:/tmp/level12$ gzip -d data.gz
bandit12@bandit:/tmp/level12$ file data
data: POSIX tar archive (GNU)
bandit12@bandit:/tmp/level12$ mv data data.tar
bandit12@bandit:/tmp/level12$ tar xvf data.tar
data5.bin
bandit12@bandit:/tmp/level12$ file data5.bin
data5.bin: POSIX tar archive (GNU)
bandit12@bandit:/tmp/level12$ mv data5.bin data5.tar
bandit12@bandit:/tmp/level12$ tar xvf data5.tar
data6.bin
bandit12@bandit:/tmp/level12$ file data6.bin
data6.bin: bzip2 compressed data, block size = 900k
bandit12@bandit:/tmp/level12$ mv data6.bin data6.tar
bandit12@bandit:/tmp/level12$ tar xvf data6.tar
data8.bin
bandit12@bandit:/tmp/level12$ file data8.bin
data8.bin: gzip compressed data, was "data9.bin", last modified: Thu May 7 18:14:30 2020, max compression, from Unix
bandit12@bandit:/tmp/level12$ mv data8.bin data8.gz
bandit12@bandit:/tmp/level12$ gzip -d data8.gz
bandit12@bandit:/tmp/level12$ file data8
data8: ASCII text
bandit12@bandit:/tmp/level12$ cat data8
The password is 8ZjyCRiBWFYkneahHwxCv3wb2a1ORpYL
bandit12@bandit:~$ rm -rf /tmp/level12/Level 13 to 14
The password for the next level is stored in /etc/bandit_pass/bandit14 and can only be read by user bandit14. For this level, you don’t get the next password, but you get a private SSH key that can be used to log into the next level.
bandit13@bandit:~$ ls
sshkey.private
~$ssh -i sshkey.private bandit14@localhost
Are you sure you want to continue connecting (yes/no)? yes
Welcome to OverTheWire!
Enjoy your stay!
bandit14@bandit:~$ whoami
bandit14
bandit14@bandit:~$ cat /etc/bandit_pass/bandit14
4wcYUJFw0k0XLShlDzztnTBHiqxU3b3eLevel 14 to 15
The password for the next level can be retrieved by submitting the password of the current level to port 30000 on localhost.
bandit14@bandit:~$ telnet localhost 30000
Trying 127.0.0.1...
Connected to localhost.
Escape character is '^]'.
4wcYUJFw0k0XLShlDzztnTBHiqxU3b3e #Bandit14 password
Correct!
BfMYroe26WYalil77FoDi9qh59eK5xNr
Connection closed by foreign host.Level 15 to 16
The password for the next level can be retrieved by submitting the password of the current level to port 30001 on localhost using SSL encryption.
bandit15@bandit:~$ openssl
OpenSSL> s_client -connect localhost:30001
CONNECTED(00000003)
depth=0 CN = localhost
verify error:num=18:self signed certificate
verify return:1
depth=0 CN = localhost
verify return:1
---
Certificate chain
0 s:/CN=localhost
i:/CN=localhost
---
Server certificate
-----BEGIN CERTIFICATE-----
MIICBjCCAW+gAwIBAgIEXcVbPTANBgkqhkiG9w0BAQUFADAUMRIwEAYDVQQDDAls
b2NhbGhvc3QwHhcNMjIwMzA5MTk0NzQyWhcNMjMwMzA5MTk0NzQyWjAUMRIwEAYD
VQQDDAlsb2NhbGhvc3QwgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBALDCas6k
DHxTRoxVISHtXOeCwJ8Sax5BZN76Hle8AH6pYTAdv9/FRssWL1xppFAtiGnFvglu
95FJvHEQirY4F0oPBTbtGU2xhzZzkWRL5Yj2C3Q2c99cyh+uWQT7sXPtB8W1osPc
YIo83YkXiArpt28474ZYdl+ohbPtP1oQHBv3AgMBAAGjZTBjMBQGA1UdEQQNMAuC
CWxvY2FsaG9zdDBLBglghkgBhvhCAQ0EPhY8QXV0b21hdGljYWxseSBnZW5lcmF0
ZWQgYnkgTmNhdC4gU2VlIGh0dHBzOi8vbm1hcC5vcmcvbmNhdC8uMA0GCSqGSIb3
DQEBBQUAA4GBAC2693WiK/kXMCauf1fEg5DwuxIfm0saYKiLSceyZo1G4IggqOBO
9JCtvMIV/xRAmYEnPvJmf0JtYv+2fsicaPh9E1GRmU0vGoYDZzA7NTZOgRmHlRKe
ihh/XSGrY7tE1qU+EfizmhcB35iZ7W5INIKlu7oyBWcvk3rI4jtPQeZp
-----END CERTIFICATE-----
subject=/CN=localhost
issuer=/CN=localhost
---
No client certificate CA names sent
Peer signing digest: SHA512
Server Temp Key: X25519, 253 bits
---
SSL handshake has read 1019 bytes and written 269 bytes
Verification error: self signed certificate
---
New, TLSv1.2, Cipher is ECDHE-RSA-AES256-GCM-SHA384
Server public key is 1024 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES256-GCM-SHA384
Session-ID: BE661254B2BBEF90054E5C170F5236371C0398F77AB07ABEBA17C48888994037
Session-ID-ctx:
Master-Key: FCF2D2A58E89B8C507B64DDE7F1FD4D17F3CD0958EF557E1827888764275B044CF542A8E30C74017B24231A788BA3B5E
PSK identity: None
PSK identity hint: None
SRP username: None
TLS session ticket lifetime hint: 7200 (seconds)
TLS session ticket:
0000 - d3 53 01 d9 4c 2e 82 50-ef 16 38 c5 d8 1b dd f2 .S..L..P..8.....
0010 - 62 63 e2 4b cb bd 5c 4e-5a 46 ad 3e 9f 16 27 10 bc.K..\NZF.>.. .
0020 - e1 4e c5 7b 4b 15 70 d1-ed 02 d9 13 1e 81 f4 b0 .N.{K.p.........
0030 - b1 41 19 54 77 6f a0 e8-14 56 e2 0b 95 cc fe 93 .A.Two...V......
0040 - 98 dc 65 04 07 6c fe 20-fe 52 e6 f8 2c 30 97 5d ..e..l. .R..,0.]
0050 - ed e2 4e b2 f6 6f 56 93-ef ba f8 8f 3d 1e 53 71 ..N..oV.....=.Sq
0060 - bb f7 ae 0c 80 83 ae 49-5f 16 96 51 f0 fc 46 59 .......I_..Q..FY
0070 - 41 b5 6f ed cc 62 ff 30-4b 12 f7 95 82 c1 c1 4f A.o..b.0K......O
0080 - 25 d7 48 e7 5c 16 54 31-8c 38 d0 f4 d7 ca d4 8f %.H.\.T1.8......
0090 - d3 bd ab 3a 43 8b 0e d7-8a 28 10 57 9d 88 21 0e ...:C....(.W..!.
Start Time: 1661461462
Timeout : 7200 (sec)
Verify return code: 18 (self signed certificate)
Extended master secret: yes
---
BfMYroe26WYalil77FoDi9qh59eK5xNr
Correct!
cluFn7wTiGryunymYOu4RcffSxQluehd
closedLevel 16 to 17
The credentials for the next level can be retrieved by submitting the password of the current level to a port on localhost in the range 31000 to 32000. First find out which of these ports have a server listening on them. Then find out which of those speak SSL and which don’t. There is only 1 server that will give the next credentials, the others will simply send back to you whatever you send to it.
bandit16@bandit:~$ nmap -A -T4 localhost -p 31000-32000
Starting Nmap 7.40 ( https://nmap.org ) at 2022-08-25 23:10 CEST
Nmap scan report for localhost (127.0.0.1)
Host is up (0.00025s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
31046/tcp open echo
31518/tcp filtered unknown
31691/tcp open echo
31790/tcp open ssl/unknown
| fingerprint-strings:
| FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, Help, Kerberos, LDAPSearchReq, LPDString, RTSPRequest, SIPOptions, SSLSessionReq, TLSSessionReq:
|\_ Wrong! Please enter the correct current password
| ssl-cert: Subject: commonName=localhost
| Subject Alternative Name: DNS:localhost
| Not valid before: 2022-08-04T14:47:02
|\_Not valid after: 2023-08-04T14:47:02
|\_ssl-date: TLS randomness does not represent time
31960/tcp open echo
bandit16@bandit:~$ openssl
OpenSSL> s_client -connect localhost:31790 -quiet
depth=0 CN = localhost
verify error:num=18:self signed certificate
verify return:1
depth=0 CN = localhost
verify return:1
cluFn7wTiGryunymYOu4RcffSxQluehd
Correct!
-----BEGIN RSA PRIVATE KEY-----
MIIEogIBAAKCAQEAvmOkuifmMg6HL2YPIOjon6iWfbp7c3jx34YkYWqUH57SUdyJ
imZzeyGC0gtZPGujUSxiJSWI/oTqexh+cAMTSMlOJf7+BrJObArnxd9Y7YT2bRPQ
Ja6Lzb558YW3FZl87ORiO+rW4LCDCNd2lUvLE/GL2GWyuKN0K5iCd5TbtJzEkQTu
DSt2mcNn4rhAL+JFr56o4T6z8WWAW18BR6yGrMq7Q/kALHYW3OekePQAzL0VUYbW
JGTi65CxbCnzc/w4+mqQyvmzpWtMAzJTzAzQxNbkR2MBGySxDLrjg0LWN6sK7wNX
x0YVztz/zbIkPjfkU1jHS+9EbVNj+D1XFOJuaQIDAQABAoIBABagpxpM1aoLWfvD
KHcj10nqcoBc4oE11aFYQwik7xfW+24pRNuDE6SFthOar69jp5RlLwD1NhPx3iBl
J9nOM8OJ0VToum43UOS8YxF8WwhXriYGnc1sskbwpXOUDc9uX4+UESzH22P29ovd
d8WErY0gPxun8pbJLmxkAtWNhpMvfe0050vk9TL5wqbu9AlbssgTcCXkMQnPw9nC
YNN6DDP2lbcBrvgT9YCNL6C+ZKufD52yOQ9qOkwFTEQpjtF4uNtJom+asvlpmS8A
vLY9r60wYSvmZhNqBUrj7lyCtXMIu1kkd4w7F77k+DjHoAXyxcUp1DGL51sOmama
+TOWWgECgYEA8JtPxP0GRJ+IQkX262jM3dEIkza8ky5moIwUqYdsx0NxHgRRhORT
8c8hAuRBb2G82so8vUHk/fur85OEfc9TncnCY2crpoqsghifKLxrLgtT+qDpfZnx
SatLdt8GfQ85yA7hnWWJ2MxF3NaeSDm75Lsm+tBbAiyc9P2jGRNtMSkCgYEAypHd
HCctNi/FwjulhttFx/rHYKhLidZDFYeiE/v45bN4yFm8x7R/b0iE7KaszX+Exdvt
SghaTdcG0Knyw1bpJVyusavPzpaJMjdJ6tcFhVAbAjm7enCIvGCSx+X3l5SiWg0A
R57hJglezIiVjv3aGwHwvlZvtszK6zV6oXFAu0ECgYAbjo46T4hyP5tJi93V5HDi
Ttiek7xRVxUl+iU7rWkGAXFpMLFteQEsRr7PJ/lemmEY5eTDAFMLy9FL2m9oQWCg
R8VdwSk8r9FGLS+9aKcV5PI/WEKlwgXinB3OhYimtiG2Cg5JCqIZFHxD6MjEGOiu
L8ktHMPvodBwNsSBULpG0QKBgBAplTfC1HOnWiMGOU3KPwYWt0O6CdTkmJOmL8Ni
blh9elyZ9FsGxsgtRBXRsqXuz7wtsQAgLHxbdLq/ZJQ7YfzOKU4ZxEnabvXnvWkU
YOdjHdSOoKvDQNWu6ucyLRAWFuISeXw9a/9p7ftpxm0TSgyvmfLF2MIAEwyzRqaM
77pBAoGAMmjmIJdjp+Ez8duyn3ieo36yrttF5NSsJLAbxFpdlc1gvtGCWW+9Cq0b
dxviW8+TFVEBl1O4f7HVm6EpTscdDxU+bCXWkfjuRb7Dy9GOtt9JPsX8MBTakzh3
vBgsyi/sN3RqRBcGU40fOoZyfAMT8s1m/uYv52O6IgeuZ/ujbjY=
-----END RSA PRIVATE KEY-----
OpenSSL> exit
bandit16@bandit:~$ mkdir /tmp/level16/ && vim private_key
#paste RSA private key
bandit16@bandit:~$ cd /tmp/level16to17/
bandit16@bandit:/tmp/level16to17$ chmod 400 private_key
bandit16@bandit:/tmp/level16to17$ ssh -i private_key bandit17@localhost
ECDSA key fingerprint is SHA256:98UL0ZWr85496EtCRkKlo20X3OPnyPSB5tB5RPbhczc.
Are you sure you want to continue connecting (yes/no)? yes
Welcome to OverTheWire!
Enjoy your stay!
bandit17@bandit:~$ whoami
bandit17
bandit17@bandit:~$ cat /etc/bandit_pass/bandit17
xLYVMN9WE5zQ5vHacb0sZEVqbrp7nBTnLevel 17 to 18
There are 2 files in the homedirectory: passwords.old and passwords.new. The password for the next level is in passwords.new and is the only line that has been changed between passwords.old and passwords.new.
bandit17@bandit:~$ ls
passwords.new passwords.old
bandit17@bandit:~$ diff passwords.new passwords.old
42c42
< kfBf3eYk5BPBRzwjqutbbfE887SVc5Yd #passwords.new
---
> w0Yfolrc5bwjS4qw5mq1nnQi6mF03bii #passwords.oldLevel 18 to 19
The password for the next level is stored in a file readme in the homedirectory. Unfortunately, someone has modified .bashrc to log you out when you log in with SSH.
$ ssh bandit18@bandit.labs.overthewire.org -p 2220
Welcome to OverTheWire!
Enjoy your stay!
Byebye !
Connection to bandit.labs.overthewire.org closed.
$ ssh -t bandit18@bandit.labs.overthewire.org -p 2220 /bin/sh
This is a OverTheWire game server. More information on http://www.overthewire.org/wargames
bandit18@bandit.labs.overthewire.org s password:
$ ls
readme
$ cat readme
IueksS7Ubh8G3DCwVzrTd8rAVOwq3M5xLevel 19 to 20
To gain access to the next level, you should use the setuid binary in the homedirectory. Execute it without arguments to find out how to use it. The password for this level can be found in the usual place (/etc/bandit_pass), after you have used the setuid binary.
bandit19@bandit:~$ ls -l
total 8
-rwsr-x--- 1 bandit20 bandit19 7296 May 7 2020 bandit20-do
bandit19@bandit:~$ ./bandit20-do
Run a command as another user.
Example: ./bandit20-do id
bandit19@bandit:~$ ./bandit20-do whoami
bandit20
bandit19@bandit:~$ ./bandit20-do cat /etc/bandit_pass/bandit20
GbKksEFF4yrVs6il55v6gwY5aVje5f0jLevel 20 to 21
There is a setuid binary in the homedirectory that does the following: it makes a connection to localhost on the port you specify as a commandline argument. It then reads a line of text from the connection and compares it to the password in the previous level (bandit20). If the password is correct, it will transmit the password for the next level (bandit21).
bandit20@bandit:~$ ls
suconnect
bandit20@bandit:~$ ./suconnect
Usage: ./suconnect <portnumber>
This program will connect to the given port on localhost using TCP. If it receives the correct password from the other side, the next password is transmitted back.
bandit20@bandit:~$ screen
#second screen
bandit20@bandit:~$ nc -lvnp 9000
listening on [any] 9000 ...
#type last obtained password
GbKksEFF4yrVs6il55v6gwY5aVje5f0j
#original screen
bandit20@bandit:~$ ./suconnect 9000
Read: GbKksEFF4yrVs6il55v6gwY5aVje5f0j
Password matches, sending next password
#return to second screen
bandit20@bandit:~$ nc -lvnp 9000
listening on [any] 9000 ...
GbKksEFF4yrVs6il55v6gwY5aVje5f0j
connect to [127.0.0.1] from (UNKNOWN) [127.0.0.1] 40682
gE269g2h3mw3pwgrj0Ha9Uoqen1c9DGrLevel 21 to 22
A program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.
bandit21@bandit:~$ cd /etc/cron.d/
bandit21@bandit:/etc/cron.d$ ls
cronjob_bandit15_root cronjob_bandit22 cronjob_bandit24
cronjob_bandit17_root cronjob_bandit23 cronjob_bandit25_root
bandit21@bandit:/etc/cron.d$ cat cronjob_bandit22
@reboot bandit22 /usr/bin/cronjob_bandit22.sh &> /dev/null
* * * * * bandit22 /usr/bin/cronjob_bandit22.sh &> /dev/null
bandit21@bandit:/etc/cron.d$ cat /usr/bin/cronjob_bandit22.sh
#!/bin/bash
chmod 644 /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv
cat /etc/bandit_pass/bandit22 > /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv
bandit21@bandit:/etc/cron.d$ cat /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv
Yk7owGAcWjwMVRwrTesJEwB7WVOiILLILevel 22 to 23
A program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.
bandit22@bandit:~$ ls -la /etc/cron.d/
total 36
drwxr-xr-x 2 root root 4096 Jul 11 2020 .
drwxr-xr-x 87 root root 4096 May 14 2020 ..
-rw-r--r-- 1 root root 62 May 14 2020 cronjob_bandit15_root
-rw-r--r-- 1 root root 62 Jul 11 2020 cronjob_bandit17_root
-rw-r--r-- 1 root root 120 May 7 2020 cronjob_bandit22
-rw-r--r-- 1 root root 122 May 7 2020 cronjob_bandit23
-rw-r--r-- 1 root root 120 May 14 2020 cronjob_bandit24
-rw-r--r-- 1 root root 62 May 14 2020 cronjob_bandit25_root
-rw-r--r-- 1 root root 102 Oct 7 2017 .placeholder
bandit22@bandit:~$ cat /etc/cron.d/cronjob_bandit23
@reboot bandit23 /usr/bin/cronjob_bandit23.sh &> /dev/null
* * * * * bandit23 /usr/bin/cronjob_bandit23.sh &> /dev/null
bandit22@bandit:~$ cat /usr/bin/cronjob_bandit23.sh
#!/bin/bash
myname=$(whoami)
mytarget=$(echo I am user $myname | md5sum | cut -d ' ' -f 1)
echo "Copying passwordfile /etc/bandit_pass/$myname to /tmp/$mytarget"
cat /etc/bandit_pass/$myname > /tmp/$mytarget
bandit22@bandit:~$ /usr/bin/cronjob_bandit23.sh
Copying passwordfile /etc/bandit_pass/bandit22 to /tmp/8169b67bd894ddbb4412f91573b38db3
bandit22@bandit:~$ cat /tmp/8169b67bd894ddbb4412f91573b38db3
Yk7owGAcWjwMVRwrTesJEwB7WVOiILLI
bandit22@bandit:~$ (echo I am user bandit23 | md5sum | cut -d ' ' -f 1)
8ca319486bfbbc3663ea0fbe81326349
bandit22@bandit:~$ cat /tmp/8ca319486bfbbc3663ea0fbe81326349
jc1udXuA1tiHqjIsL8yaapX5XIAI6i0nLevel 23 to 24
A program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.
bandit23@bandit:~$ ls -lsa /etc/cron.d
total 36
4 drwxr-xr-x 2 root root 4096 Jul 11 2020 .
4 drwxr-xr-x 87 root root 4096 May 14 2020 ..
4 -rw-r--r-- 1 root root 62 May 14 2020 cronjob_bandit15_root
4 -rw-r--r-- 1 root root 62 Jul 11 2020 cronjob_bandit17_root
4 -rw-r--r-- 1 root root 120 May 7 2020 cronjob_bandit22
4 -rw-r--r-- 1 root root 122 May 7 2020 cronjob_bandit23
4 -rw-r--r-- 1 root root 120 May 14 2020 cronjob_bandit24
4 -rw-r--r-- 1 root root 62 May 14 2020 cronjob_bandit25_root
4 -rw-r--r-- 1 root root 102 Oct 7 2017 .placeholder
bandit23@bandit:~$ cat /etc/cron.d/cronjob_bandit24
@reboot bandit24 /usr/bin/cronjob_bandit24.sh &> /dev/null
* * * * * bandit24 /usr/bin/cronjob_bandit24.sh &> /dev/null
bandit23@bandit:~$ cat /usr/bin/cronjob_bandit24.sh
#!/bin/bash
myname=$(whoami)
cd /var/spool/$myname
echo "Executing and deleting all scripts in /var/spool/$myname:"
for i in * .*;
do
if [ "$i" != "." -a "$i" != ".." ];
then
echo "Handling $i"
owner="$(stat --format "%U" ./$i)"
if [ "${owner}" = "bandit23" ]; then
timeout -s 9 60 ./$i
fi
rm -f ./$i
fi
done
bandit23@bandit:~$ mkdir /tmp/bandit23/
bandit23@bandit:~$ cd /tmp/bandit23/
bandit23@bandit:/tmp/bandit23$ vim script.sh
#remove first # from each line
##! /bin/sh
#cat /etc/bandit_pass/bandit24 >> /tmp/bandit23/bandit24_pass
#done
bandit23@bandit:/tmp/bandit23$ chmod 777 script.sh
bandit23@bandit:/tmp/bandit23$ chmod 777 /tmp/bandit23
bandit23@bandit:/tmp/bandit23$ cp script.sh /var/spool/bandit24
bandit23@bandit:/tmp/bandit23$ ls
script.sh
#60 seconds later
bandit23@bandit:/tmp/bandit23$ ls
bandit24_pass script.sh
bandit23@bandit:/tmp/bandit23$ cat bandit24_pass
UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ
bandit23@bandit:/tmp/bandit23$ cd ~
bandit23@bandit:~$ rm -rf /tmp/bandit23/Level 24 to 25
A daemon is listening on port 30002 and will give you the password for bandit25 if given the password for bandit24 and a secret numeric 4-digit pincode. There is no way to retrieve the pincode except by going through all of the 10000 combinations, called brute-forcing.
bandit24@bandit:~$ nc localhost 30002
I am the pincode checker for user bandit25. Please enter the password for user bandit24 and the secret pincode on a single line, separated by a space.
#try first combination
UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ 1000
Wrong! Please enter the correct pincode. Try again.
Timeout. Exiting.
#Connection ends if not given correct password/4-digit number combination
bandit24@bandit:~$ mkdir /tmp/24bandit
bandit24@bandit:~$ cd /tmp/24bandit
bandit24@bandit:/tmp/24bandit$ vim script.sh
#! /bin/sh
#for PINCODE in $(seq 999 10000);do
#echo "UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ $PINCODE"
#done
bandit24@bandit:/tmp/24bandit$ chmod 777 script.sh
bandit24@bandit:/tmp/24bandit$ ./script.sh | nc localhost 30002
I am the pincode checker for user bandit25. Please enter the password for user bandit24 and the secret pincode on a single line, separated by a space.
Wrong! Please enter the correct pincode. Try again.
Wrong! Please enter the correct pincode. Try again.
...
Wrong! Please enter the correct pincode. Try again.
Wrong! Please enter the correct pincode. Try again.
Correct!
The password of user bandit25 is uNG9O58gUE7snukf3bvZ0rxhtnjzSGzG
Exiting.
bandit24@bandit:/tmp/24bandit$ cd ~ && rm -rf /tmp/24bandit/Level 25 to 26
Logging in to bandit26 from bandit25 should be fairly easy… The shell for user bandit26 is not /bin/bash, but something else. Find out what it is, how it works and how to break out of it.
bandit25@bandit:~$ cat /etc/passwd | grep "bandit26"
bandit26:x:11026:11026:bandit level 26:/home/bandit26:/usr/bin/showtext
bandit25@bandit:~$ cat /usr/bin/showtext
#!/bin/sh
export TERM=linux
more ~/text.txt
exit 0
bandit25@bandit:~$ ssh -i bandit26.sshkey bandit26@localhost
Could not create directory '/home/bandit25/.ssh'.
The authenticity of host 'localhost (127.0.0.1)' can't be established.
ECDSA key fingerprint is SHA256:98UL0ZWr85496EtCRkKlo20X3OPnyPSB5tB5RPbhczc.
Are you sure you want to continue connecting (yes/no)? yes
Welcome to OverTheWire!
_ _ _ _ ___ __
| | | (_) | |__ \ / /
| |__ __ _ _ __ __| |_| |_ ) / /_
| '_ \ / _` | '_ \ / _` | | __| / / '_ \
| |_) | (_| | | | | (_| | | |_ / /| (_) |
|_.__/ \__,_|_| |_|\__,_|_|\__|____\___/
Connection to localhost closed.
#Must reduce the window size to enable pagination. Will look something like this
#typing vi to access screen editor and type "e: /etc/bandit_pass/bandit26"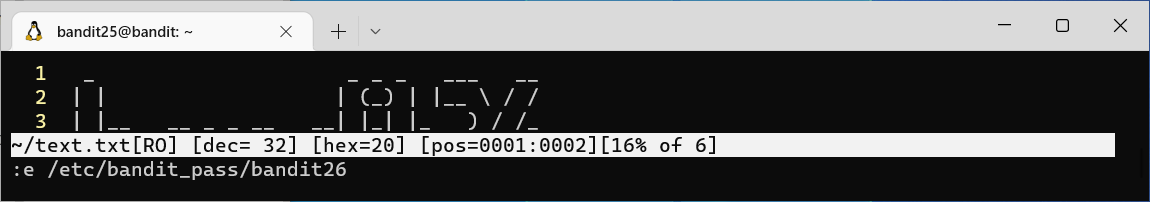
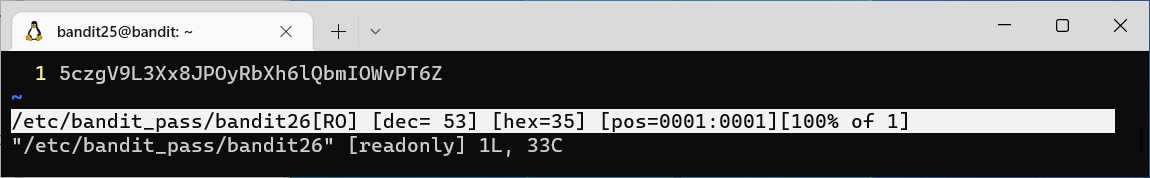
5czgV9L3Xx8JPOyRbXh6lQbmIOWvPT6ZLevel 26 to 27
Good job getting a shell! Now hurry and grab the password for bandit27!
#Change shell type.
:set shell-/bin/bash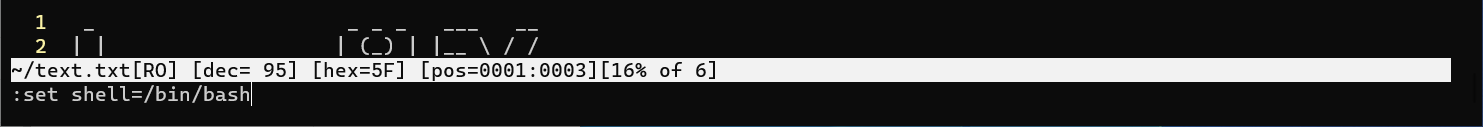
#Change into shell.
:shell
bandit26@bandit:~$ ls -la
total 36
drwxr-xr-x 3 root root 4096 May 7 2020 .
drwxr-xr-x 41 root root 4096 May 7 2020 ..
-rwsr-x--- 1 bandit27 bandit26 7296 May 7 2020 bandit27-do
-rw-r--r-- 1 root root 220 May 15 2017 .bash_logout
-rw-r--r-- 1 root root 3526 May 15 2017 .bashrc
-rw-r--r-- 1 root root 675 May 15 2017 .profile
drwxr-xr-x 2 root root 4096 May 7 2020 .ssh
-rw-r----- 1 bandit26 bandit26 258 May 7 2020 text.txt
bandit26@bandit:~$ ./bandit27-do
Run a command as another user.
Example: ./bandit27-do id
bandit26@bandit:~$ ./bandit27-do cat /etc/bandit_pass/bandit27
3ba3118a22e93127a4ed485be72ef5eaLevel 27 to 28
There is a git repository at ssh://bandit27-git@localhost/home/bandit27-git/repo. The password for the user bandit27-git is the same as for the user bandit27.
Clone the repository and find the password for the next level.
bandit27@bandit:~$ mkdir /tmp/27bandit/ && cd /tmp/27bandit/
bandit27@bandit:/tmp/27bandit$ git clone ssh://bandit27-git@localhost/home/bandit27-git/repo
bandit27-git@localhost password:
remote: Counting objects: 3, done.
remote: Compressing objects: 100% (2/2), done.
remote: Total 3 (delta 0), reused 0 (delta 0)
Receiving objects: 100% (3/3), done.
bandit27@bandit:/tmp/27bandit$ ls
repo
bandit27@bandit:/tmp/27bandit$ cd repo
bandit27@bandit:/tmp/27bandit/repo$ ls
README
bandit27@bandit:/tmp/27bandit/repo$ cat README
The password to the next level is: 0ef186ac70e04ea33b4c1853d2526fa2
bandit27@bandit:/tmp/27bandit/repo$ cd ~
bandit27@bandit:~$ rm -rf /tmp/27bandit/Level 28 to 29
There is a git repository at ssh://bandit28-git@localhost/home/bandit28-git/repo. The password for the user bandit28-git is the same as for the user bandit28.
Clone the repository and find the password for the next level.
bandit28@bandit:~$ mkdir /tmp/28bandit/ && cd /tmp/28bandit/
bandit28@bandit:/tmp/28bandit$ git clone ssh://bandit28-git@localhost/home/bandit28-git/repo
Cloning into 'repo'...
bandit28-git@localhosts password:
remote: Counting objects: 9, done.
remote: Compressing objects: 100% (6/6), done.
remote: Total 9 (delta 2), reused 0 (delta 0)
Receiving objects: 100% (9/9), 796 bytes | 0 bytes/s, done.
Resolving deltas: 100% (2/2), done.
bandit28@bandit:/tmp/28bandit$ ls
repo
bandit28@bandit:/tmp/28bandit$ cd repo
bandit28@bandit:/tmp/28bandit/repo$ ls
README.md
bandit28@bandit:/tmp/28bandit/repo$ cat README.md
# Bandit Notes
Some notes for level29 of bandit.
## credentials
- username: bandit29
- password: xxxxxxxxxx
bandit28@bandit:/tmp/28bandit/repo$ git log
commit edd935d60906b33f0619605abd1689808ccdd5ee
Author: Morla Porla <morla@overthewire.org>
Date: Thu May 7 20:14:49 2020 +0200
fix info leak
commit c086d11a00c0648d095d04c089786efef5e01264
Author: Morla Porla <morla@overthewire.org>
Date: Thu May 7 20:14:49 2020 +0200
add missing data
commit de2ebe2d5fd1598cd547f4d56247e053be3fdc38
Author: Ben Dover <noone@overthewire.org>
Date: Thu May 7 20:14:49 2020 +0200
initial commit of README.md
bandit28@bandit:/tmp/28bandit/repo$ git diff c086d11a00c0648d095d04c089786efef5e01264
diff --git a/README.md b/README.md
index 3f7cee8..5c6457b 100644
--- a/README.md
+++ b/README.md
@@ -4,5 +4,5 @@ Some notes for level29 of bandit.
## credentials
- username: bandit29
-- password: bbc96594b4e001778eee9975372716b2
+- password: xxxxxxxxxx
bandit28@bandit:/tmp/28bandit/repo$ cd ~/ && rm -rf /tmp/28bandit/
bandit28@bandit:~$Level 29 to 30
There is a git repository at ssh://bandit29-git@localhost/home/bandit29-git/repo. The password for the user bandit29-git is the same as for the user bandit29.
Clone the repository and find the password for the next level.
bandit29@bandit:~$ mkdir /tmp/29bandit/ && cd /tmp/29bandit/
bandit29@bandit:/tmp/29bandit$ git clone ssh://bandit29-git@localhost/home/bandit29-git/repo
Cloning into 'repo'...
bandit29-git@localhosts password:
remote: Counting objects: 16, done.
remote: Compressing objects: 100% (11/11), done.
remote: Total 16 (delta 2), reused 0 (delta 0)
Receiving objects: 100% (16/16), done.
Resolving deltas: 100% (2/2), done.
bandit29@bandit:/tmp/29bandit$ ls
repo
bandit29@bandit:/tmp/29bandit$ cd repo
bandit29@bandit:/tmp/29bandit/repo$ ls
README.md
bandit29@bandit:/tmp/29bandit/repo$ cat README.md
# Bandit Notes
Some notes for bandit30 of bandit.
## credentials
- username: bandit30
- password: <no passwords in production!>
bandit29@bandit:/tmp/29bandit/repo$ git branch -r
origin/HEAD -> origin/master
origin/dev
origin/master
origin/sploits-dev
bandit29@bandit:/tmp/29bandit/repo$ git checkout origin/dev
Note: checking out 'origin/dev'.
You are in 'detached HEAD' state. You can look around, make experimental
changes and commit them, and you can discard any commits you make in this
state without impacting any branches by performing another checkout.
If you want to create a new branch to retain commits you create, you may
do so (now or later) by using -b with the checkout command again. Example:
git checkout -b <new-branch-name>
HEAD is now at bc83328... add data needed for development
bandit29@bandit:/tmp/29bandit/repo$ ls
code README.md
bandit29@bandit:/tmp/29bandit/repo$ cat README.md
# Bandit Notes
Some notes for bandit30 of bandit.
## credentials
- username: bandit30
- password: 5b90576bedb2cc04c86a9e924ce42faf
bandit29@bandit:/tmp/29bandit/repo$ cd ~ && rm -rf /tmp/29bandit/Level 30 to 31
There is a git repository at ssh://bandit30-git@localhost/home/bandit30-git/repo. The password for the user bandit30-git is the same as for the user bandit30.
Clone the repository and find the password for the next level.
bandit30@bandit:~$ mkdir /tmp/30bandit/ && cd /tmp/30bandit/
bandit30@bandit:/tmp/30bandit$ git clone ssh://bandit30-git@localhost/home/b
andit30-git/repo
Cloning into 'repo'...
bandit30-git@localhosts password:
remote: Counting objects: 4, done.
remote: Total 4 (delta 0), reused 0 (delta 0)
Receiving objects: 100% (4/4), done.
bandit30@bandit:/tmp/30bandit$ ls
repo
bandit30@bandit:/tmp/30bandit$ cd repo
bandit30@bandit:/tmp/30bandit/repo$ ls
README.md
bandit30@bandit:/tmp/30bandit/repo$ cat README.md
just an epmty file... muahaha
bandit30@bandit:/tmp/30bandit/repo$ git tag
secret
bandit30@bandit:/tmp/30bandit/repo$ git show secret
47e603bb428404d265f59c42920d81e5
bandit30@bandit:/tmp/30bandit/repo$ cd ~ && rm -rf /tmp/30bandit/Level 31 to 32
There is a git repository at ssh://bandit31-git@localhost/home/bandit31-git/repo. The password for the user bandit31-git is the same as for the user bandit31.
Clone the repository and find the password for the next level.
bandit31@bandit:~$ mkdir /tmp/31bandit/ && cd /tmp/31bandit/
bandit31@bandit:/tmp/31bandit$ git clone ssh://bandit31-git@localhost/home/bandit31-git/repo
Cloning into 'repo'...
bandit31-git@localhosts password:
remote: Counting objects: 4, done.
remote: Compressing objects: 100% (3/3), done.
remote: Total 4 (delta 0), reused 0 (delta 0)
Receiving objects: 100% (4/4), done.
bandit31@bandit:/tmp/31bandit$ ls
repo
bandit31@bandit:/tmp/31bandit$ cd repo
bandit31@bandit:/tmp/31bandit/repo$ ls
README.md
bandit31@bandit:/tmp/31bandit/repo$ cat README.md
This time your task is to push a file to the remote repository.
Details:
File name: key.txt
Content: 'May I come in?'
Branch: master
bandit31@bandit:/tmp/31bandit/repo$ vim key.txt
bandit31@bandit:/tmp/31bandit/repo$ git add key.txt
The following paths are ignored by one of your .gitignore files:
key.txt
Use -f if you really want to add them.
bandit31@bandit:/tmp/31bandit/repo$ git add -f key.txt
bandit31@bandit:/tmp/31bandit/repo$ git commit -m "key commit"
[master 9cbf5dd] key commit
1 file changed, 1 insertion(+)
create mode 100644 key.txt
bandit31@bandit:/tmp/31bandit/repo$ git push
bandit31-git@localhosts password:
Counting objects: 3, done.
Delta compression using up to 2 threads.
Compressing objects: 100% (2/2), done.
Writing objects: 100% (3/3), 316 bytes | 0 bytes/s, done.
Total 3 (delta 0), reused 0 (delta 0)
remote: ### Attempting to validate files... ####
remote:
remote: .oOo.oOo.oOo.oOo.oOo.oOo.oOo.oOo.oOo.oOo.
remote:
remote: Well done! Here is the password for the next level:
remote: 56a9bf19c63d650ce78e6ec0354ee45e
remote:
remote: .oOo.oOo.oOo.oOo.oOo.oOo.oOo.oOo.oOo.oOo.
remote:
To ssh://localhost/home/bandit31-git/repo
! [remote rejected] master -> master (pre-receive hook declined)
error: failed to push some refs to 'ssh://bandit31-git@localhost/home/bandit31-git/repo'
bandit31@bandit:/tmp/31bandit/repo$ cd ~ && rm -rf /tmp/31bandit/Level 32 to 33
After all this git stuff its time for another escape. Good luck!
WELCOME TO THE UPPERCASE SHELL
>> $0
$ ls -lsa
total 28
4 drwxr-xr-x 2 root root 4096 May 7 2020 .
4 drwxr-xr-x 41 root root 4096 May 7 2020 ..
4 -rw-r--r-- 1 root root 220 May 15 2017 .bash_logout
4 -rw-r--r-- 1 root root 3526 May 15 2017 .bashrc
4 -rw-r--r-- 1 root root 675 May 15 2017 .profile
8 -rwsr-x--- 1 bandit33 bandit32 7556 May 7 2020 uppershell
$ cat /etc/bandit_pass/bandit33
c9c3199ddf4121b10cf581a98d51caee